
A cutting edge security system based on unique algorithm that blocks all cyber attacks within organizational networks, including Zero Day attacks.
The main problem that the product aims to solve is the increasing spread of viruses and malware within the organization, as well as saving security budget.
UX
Main End Users

System Architecture
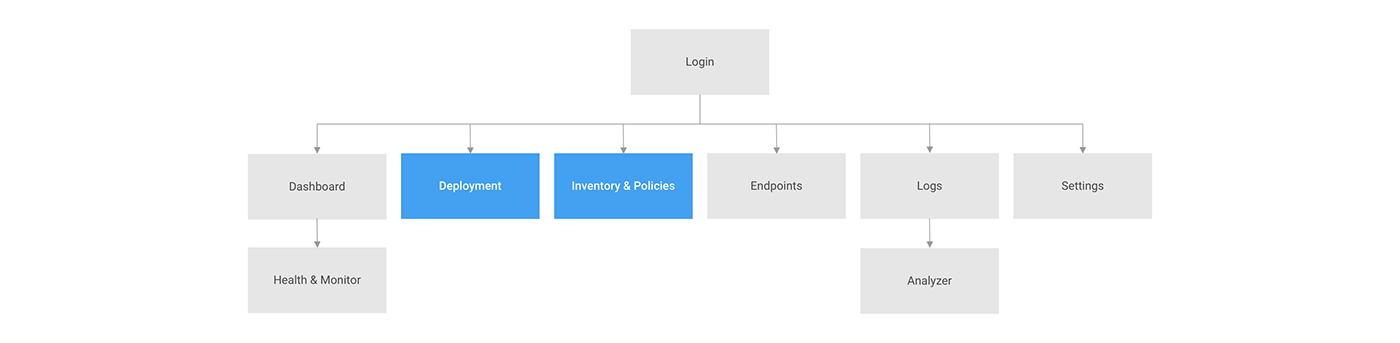
Wireframes
Deployment screen - system integration by spreading agent files across networks. the screen displays the organizational general active directory (AD) tree on the left, protected endpoints out of the AD on the right - Cyber tree. in the middle, deployment progress status.

Inventory & Policies - once the organizational Cyber tree is set, each group of endpoints or a single endpoint, display its list of approved & unapproved apps, based on deployed policy. the policy can be customized.

UI





Fonts & Colors

Components

